How to remove SuperFish malware?
- Admin
- February 18, 2016
- 1,341
A Brief Introduction
Levono in the race of generating money has put its users at risk. This is regarded as one of the biggest mistakes, which the company has made in the past. It is since the mid of the year 2014, the company has been preinstalling the Superfish malware on its PCs. Now, what is Superfish malware and how is it harmful for the users? Well, Superfish is the most popular visual search tool that features adware. This malware is used to fake the encryption certificates for every HTTPS protected website you open on your system. Basically, it works like the users are being attacked in such a way that the sites you visit are being filled with ads. This further leads you to certain security issues. Through this, the hackers can easily trap the innocent web users. This piece of content will mainly focus on how to remove Superfish malware.
The Leveno PCs which feature preinstalled Superfish
Following leveno PCs are reported to have featured preinstalled Superfish.
- U Series: U330P, U330Touch, U430P, U430Touch, U530Touch
- Z Series: Z40-70, Z40-75, Z50-70, Z50-75
- Flex Series: Flex2 14, Flex2 14(BTM), Flex2 14D, Flex2 15, Flex2 15(BTM), Flex2 15D, Flex 10
- Y Series: Y40-70, Y50-70, Y430P
- MIIX Series: MIIX2-8, MIIX2-10, MIIX2-11
- S Series: S20-30, S20-30Touch, S40-70, S310, S410, S415, S415Touch
- E Series: E10-30
- YOGA Series: YOGA2-11BTM, YOGA2-11HSW, YOGA2-13, YOGA2Pro-13
- G Series: G40-30, G40-45, G40-70, G50-30, G50-45, G50-70, G410, G510, G710
Leveno’s Guide to help users to remove superfish
The best solution of getting rid of superfish malware is to remove superfish completely. The company Leveno has published complete guide which describe how to remove the advertising software but unfortunately the guide was not adequate to remove Superfish properly. This was because it didn’t address the security vulnerability issue. But later on the company updated the instructions which defined a step to step guide to remove superfish and the security flaws as well. The company has been working on an automated clean up tool which will help the users to automatically remove superfish malware.
The Superfish root certificate is used for creating certification for any domain we have. Now these certificates are trusted by every browser installed on any Superfish infected system. This leads the innocent users prone to vulnerable attacks. For fixing this issue, the certificates are required to be completely removed. There are different many locations where Superfish certificate can be installed. Windows has got its own certificate store in which the root certificate are placed that it trusts fully. Now what Superfish do is install its own certificate to the Windows certificate store. Furthermore, we have got some third party software like Mozilla Thunderbird and Mozilla Firefox which have their private certificate stores. Superfish also install its certificate in these private certificate stores. For fixing this issue, we are required to completely clean these stores in order to make our system secure enough.
Step to Step Guide on How to remove Superfish Malware
You are required to follow the above mentioned steps in order to remove superfish malware and secure your system.
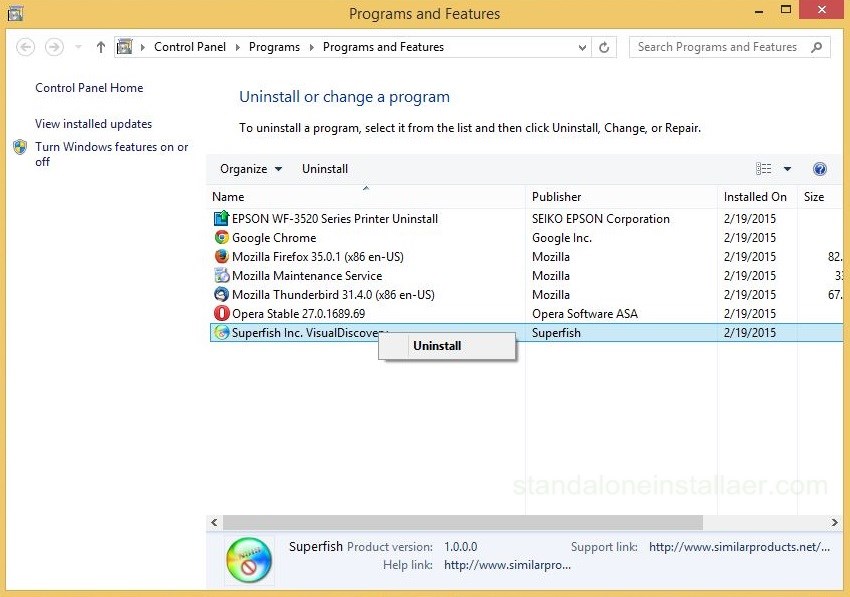
First uninstall the superfish software from your system in order to clean it. For doing this, you are required to open the Control panel, click programs and then select programs and features. The list of installed programs will appear in front of you. Now, locate the program named as "Superfish Inc. VisualDiscovery". Simply right click on it and click Uninstall. After few seconds, the software will be removed successfully. You can now reboot your system.
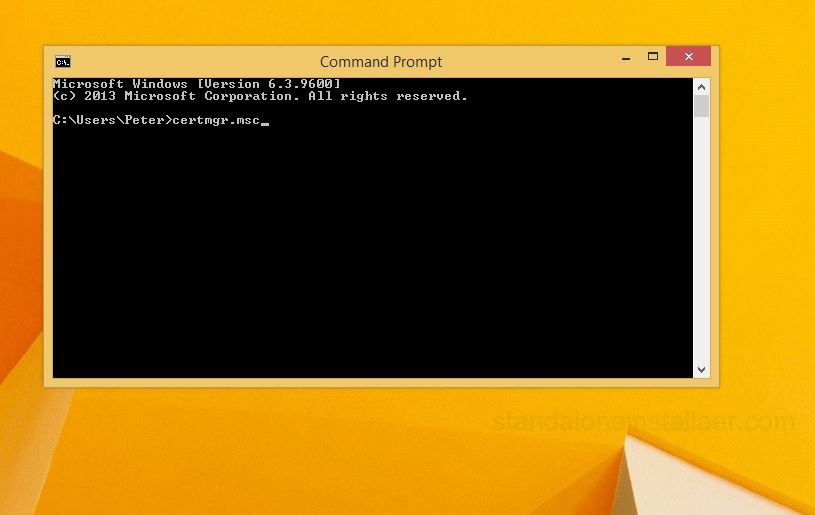
The next step is to clean up the Windows certificate store. For doing that, you are required to open the start menu and selecting the command prompt. After that enter the command certmgr.msc and press enter.
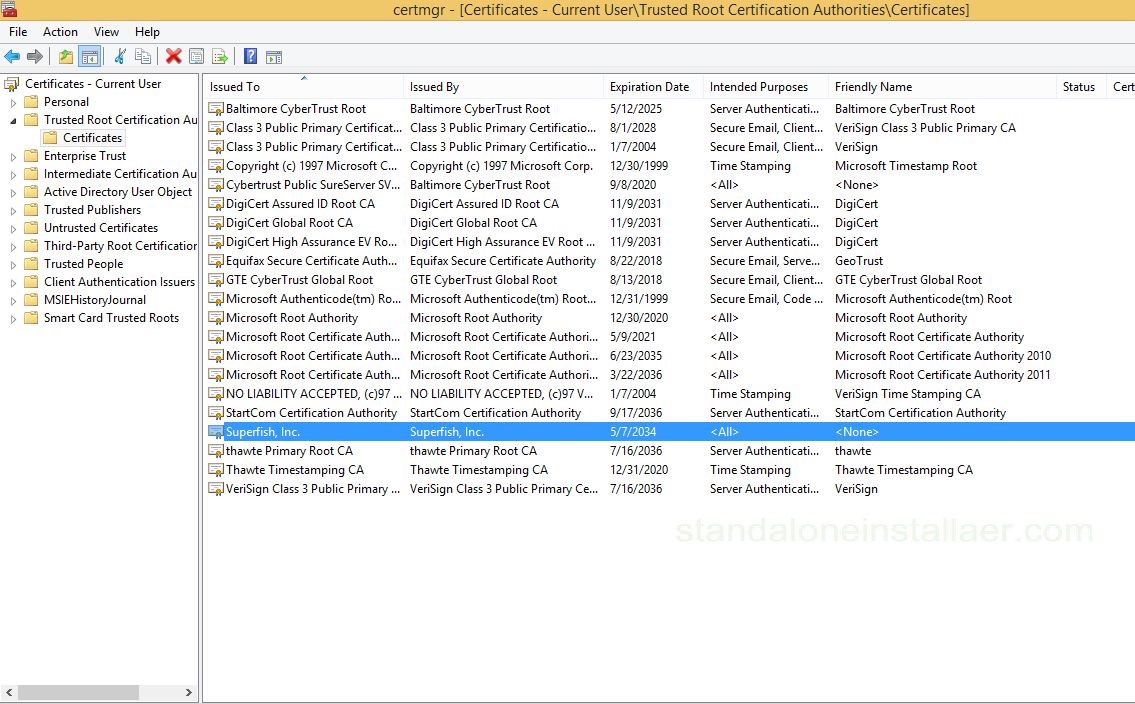
- This will open the Windows certificate manager app. On the left side, the folder “Trusted Root Certification Authorities” is located. Open its subfolder “Certificates”. The list of the certificate authorities trusted by Windows will appear. One of these will be titled as “Superfish, Inc”. Select it and choose delete. Be sure that you only delete the Superfish certificate.
If you are using Chrome, Internet Explorer, Opera and don’t use Mozilla Thunderbird or Mozilla Firefox then you are not at any risky point. Because all these browsers use the system certificate store and are protected enough.
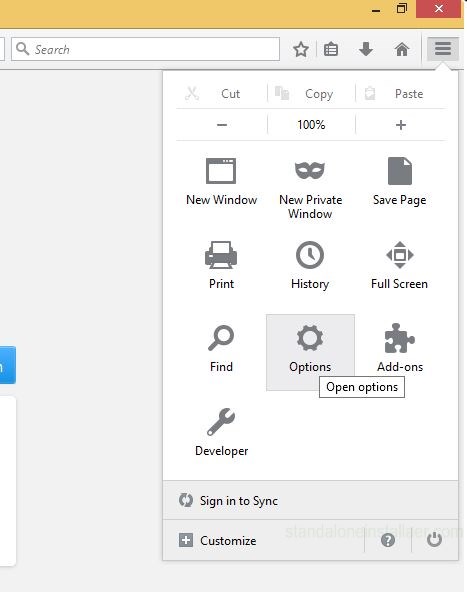
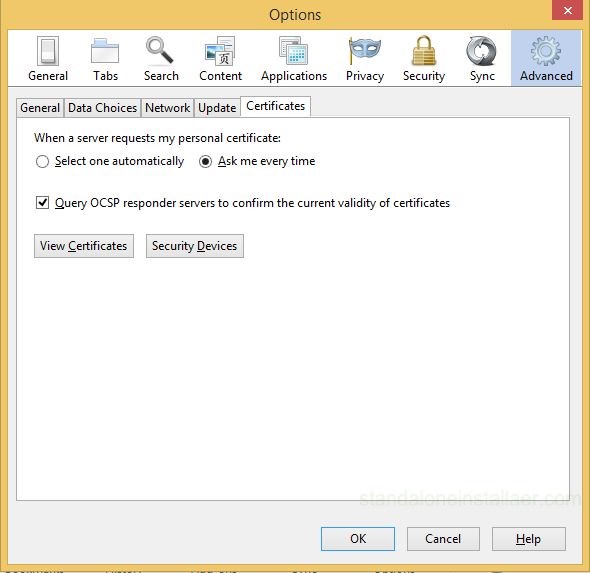
However, if you are having Mozilla Firefox then you need to remove Superfish certificate. For this, open the menu which is located in the top right, select options
and then choose the Advanced tab. Select the Certificates sub tab.
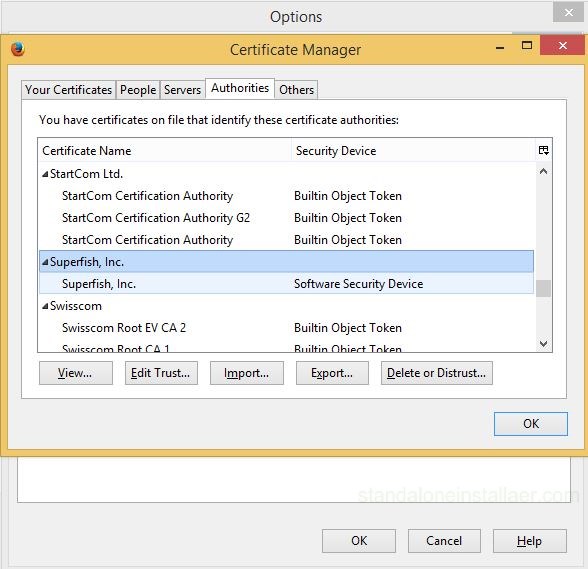
Here View Certificates so that you can view the complete list of trusted certificates. Here select the Superfish entry which includes the lines “Software Security Device”. After selecting, press “Delete or Distrust” option.
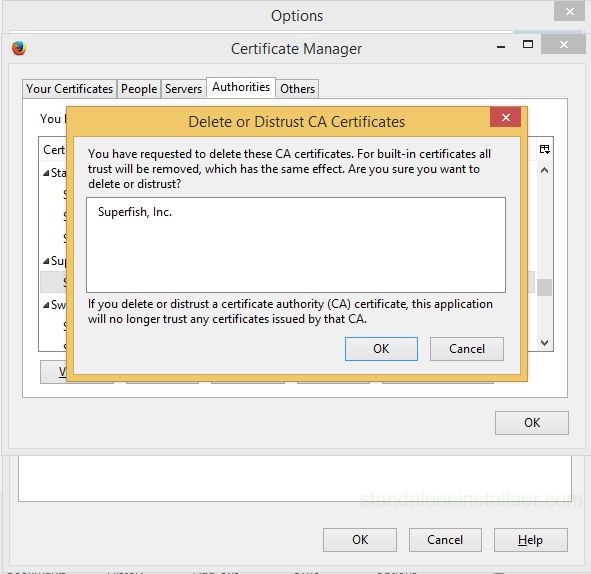
Firefox will ask you again if you really wish to delete it. Press OK to confirm.
The same process will be followed for Mozilla Thunderbird. Just the options, menus and dialog boxes look different.
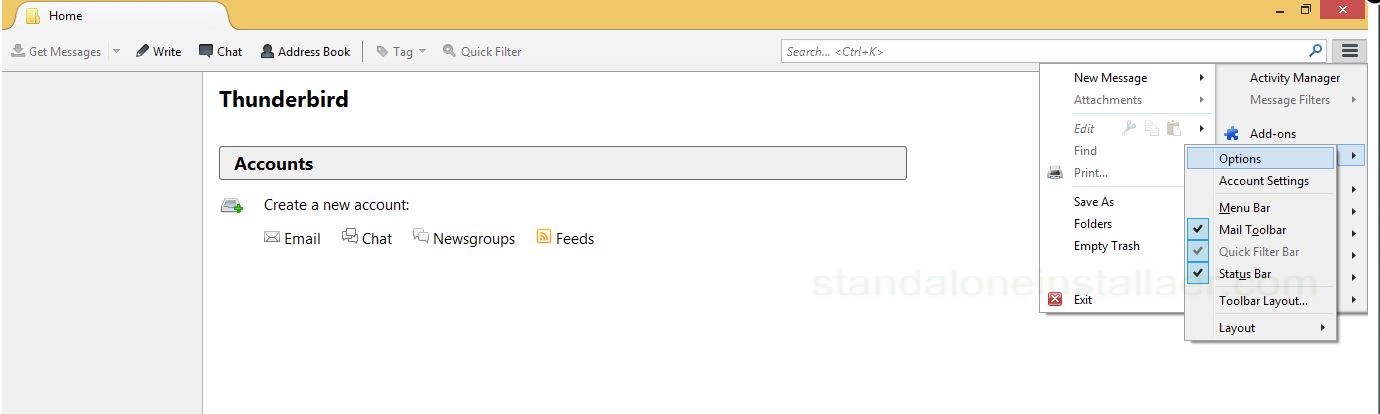
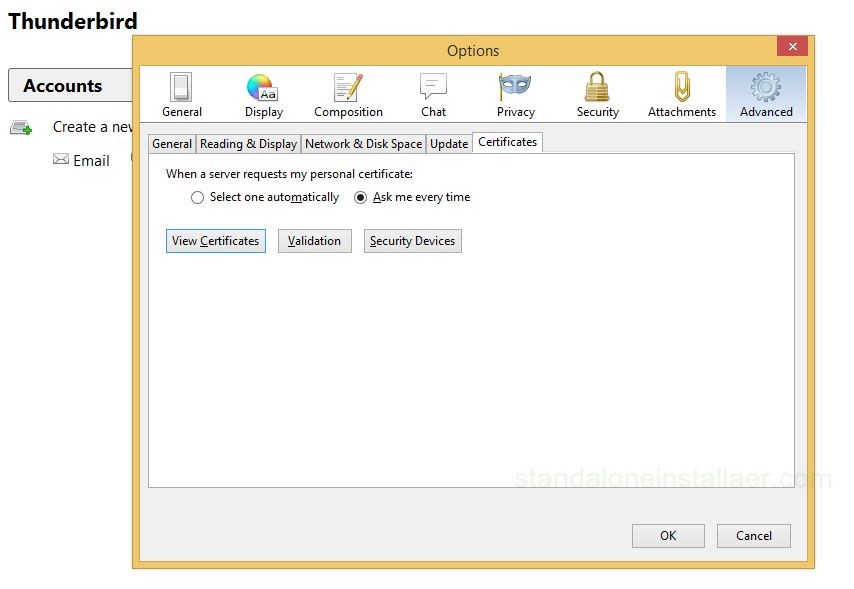
For Mozilla Thunderbird, choose Options
and then go to the Certificate sub tab of the Advanced option.
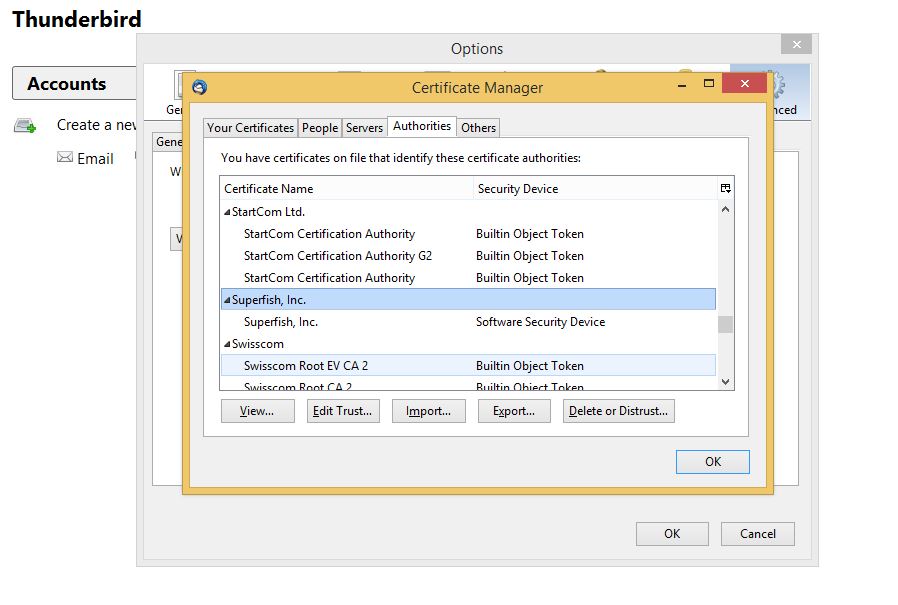
After that choose View Certificates and here locate the Superfish entry.
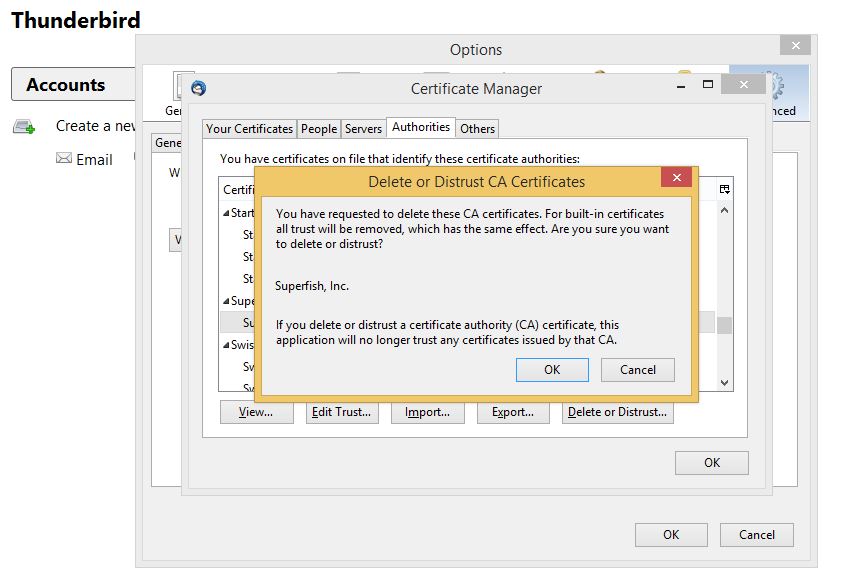
Choose Superfish entry and click Delete or Distrust button. Confirm it by pressing OK.
-
Finally you are down with the process of deleting the superfish certificates. Now you are safe and secure from any kind of Superfish certificate.
Note:
Note that if the system has multiple users, then you are required to repeat the same certificate removal process for each user. The following mentioned steps only remove the Superfish root certificate for the current user who is logged in at a time. Your system should be now free from the Superfish malware threats or Superfish adware infection. Hope the complete step to step guide on how to remove superfish helps you getting rid of superfish. If you have any queries, feel free to ask in the comment section below. Stay locked to us.